Summary:
This article is a brief overview of the different types of access tokens and their specific use cases. Read on to learn more about OAuth 2.0. Access tokens.
OAuth 2.0 Grant Types With Their Use Cases 1
- Authorization code grant
- Implicit grant
- Resource owner credentials grant
- Client credentials grant
- Refresh token grant
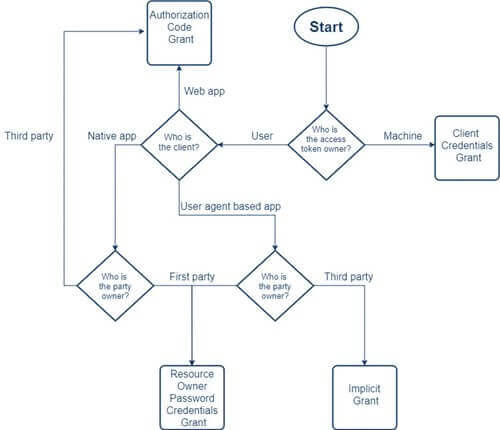
The way an application (be it a web app, naïve app, or server-to-server application) gets an access token is what a grant type means in OAuth 2.0. Access tokens are what allow access to specific defined server resources. In simpler terms, they grant permission to a client to access some protected resources.
If you are building a modern application, you would most likely want to know whether your end-user is authenticated or not to ensure that your APIs are protected from unauthenticated users. For this purpose, you can issue your authenticated users signed access tokens passed through your app to grant them access.
There are several ways (or grants) of acquiring access tokens. Let’s discuss these different grant types and their specific use cases to help you decide which type must implement to ensure the kind of experience you’d want your users to have.
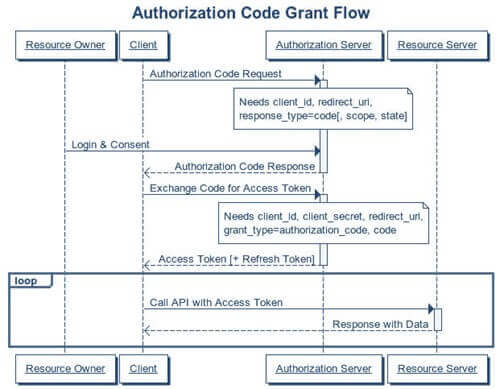
1. Authorization code grant
- Have you ever signed into application using your Facebook or Google account? If yes, the chances are that you’ve already come across this grant type.
- This grant type has a few benefits over the other types such as the access token remains invisible to the user, which means it is a highly secure way of passing the token back to the application.
- Response type=code, the client-id, redirect-uri, scope, and state are the authorization grant parameters used to build this grant type.
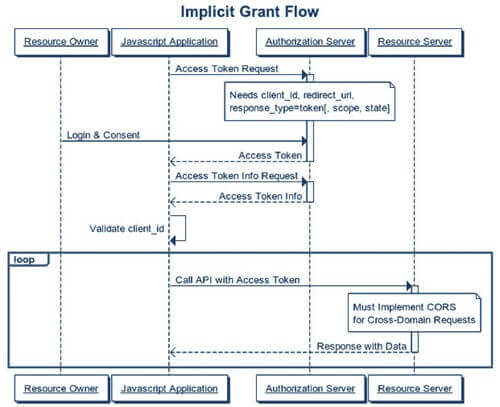
2. Implicit grant
- The most appropriate use case for this grant type is a single-page JavaScript app which is easily accessible and doesn’t have a way to store client secrets safely.
- In this grant flow, the user is redirected to the authorization server which validates the parameters in the query string. After that, the use is required to login to the server and approve the app’s request. On accepting it, he gets redirected back to the application with an access token.
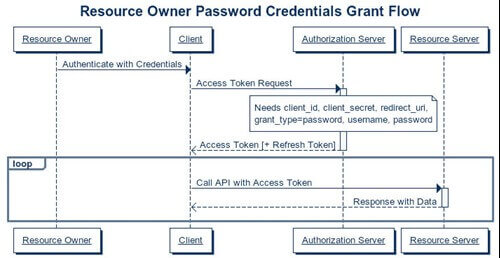
3. Resource owner credentials grant
- This type of grant is suitable for clients who have a trust relationship with their resource owners and can obtain their credentials. Also, clients who use direct authentication schemes but want to migrate to OAuth can consider using this grant type.
- Both web and native device applications are suitable to acquire access token through this grant type.
4. Client credentials grant
- The best use case for this grant type lies for clients who want to obtain an access token outside the context of a user meaning they do not require the permission of a specific user to access data.
- To implement this grant type, the client requests an access token after which the app’s credential get validated. On successful validation, the access token gets returned to the client, and with the valid access token, the client calls the protected API.

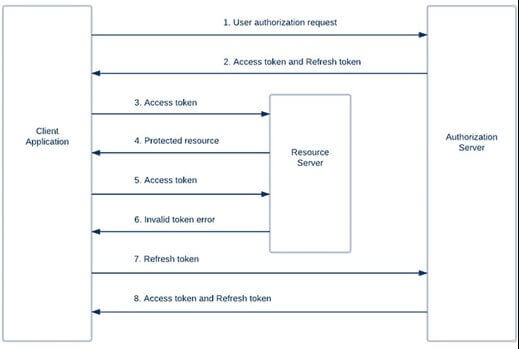
5. Refresh token grant
Access tokens eventually expire, and with that, a client’s authorization of a user’s resource expires too. This is where the Refresh token grant comes into the picture and allows clients continued access to a user’s resource